Software security is the process of building and protecting a piece of software in such a manner that no external or internal malicious attempts or coding errors may lead to unfortunate circumstances such as loss of data, loss of privacy, hacking of software etc. In today’s day and age, the world is slowly turning into a huge digital family, especially with the advent and rise in popularity of Social Networking platforms like Facebook, Instagram and Snap chat. These sites facilitate online interactions of multiple users all over the globe through the sharing and receiving of private data. This sharing of personal data leads to many security issues concerning privacy, trust and authorization which needs to be handled with utmost care. Software security thus plays a defining role in the Software Engineering process.
Software engineering process follows a fixed set of ‘timeline’. It is known as SDLC(Software Development Life Cycle). The key elements of such a Life cycle are Requirement Gathering and Analysis, Design, Implementation(Code and Compilation), Tests, Results, Deploy, Feedback/Maintenance.
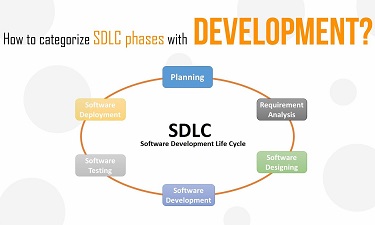
However, these steps lack the term ‘Security’. Most of such applications once made are still vulnerable to most of the exploitations. Even if the developers do consider the security aspect, they would include it in the end with another step between S/W development and S/W testing named Security modifications. However, the changes in each and every part would expose the software more and thus, the software would still be vulnerable.
A solution to such a problem is the inclusion of security check-ups between different operations. For example:- checking of Abuse cases, risk analysis and patching up of the system. Such a cycle would then be a combination of ‘Security Cycle’ and ‘SDLC’. Thus the term would arise named ‘Secure Software Life Cycle’.
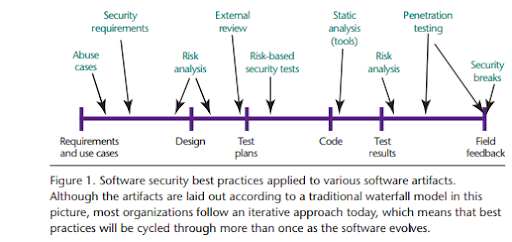
However, the inclusion of such cases between different operations would consume time. In a fast-moving world, such a case is not ‘time-favoured’. We would need a quicker and effective cycle, which would be advantageous as well as efficient.
I have included some Secure Life Cycle points which can be included during development to improve upon security. The points are as follows:-